前言
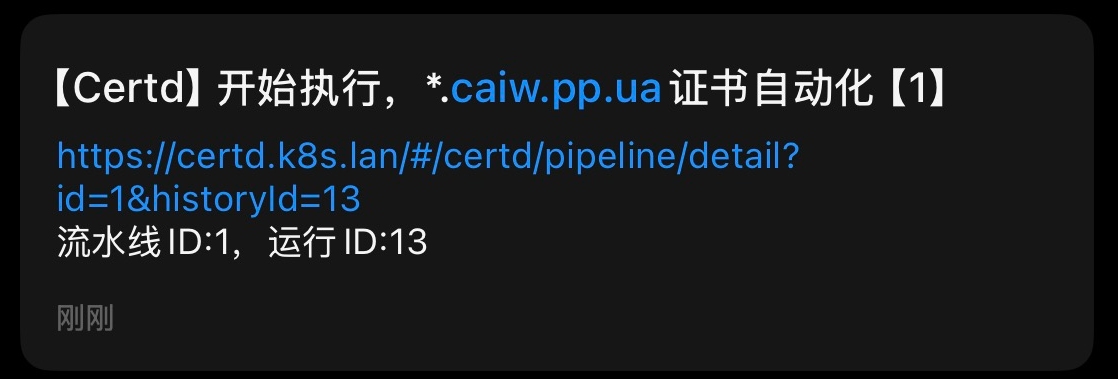
前段时间去办了商宽,可算是有公网IP了 CloudFlare Tunnel实在太慢了
然后我白嫖了免费的pp.ua域名托管到了CF 现在只需要定期给域名申请证书就好了
开始折腾
搜了一圈发现有个叫Certd的方案不错,类似于Certimates,不过这个有些功能要收费并且更强大
但其实他已经把东西开放出来了()收费的地方自己写也是能实现的
我需要的就是让他自动把证书部署到雷池WAF,因为我所有暴露到公网的服务都由雷池WAF提供
搭建
Certd我就直接照着原来的compose部署到K8s上就好
这里放上yml
---
apiVersion: apps/v1
kind: Deployment
metadata:
annotations: {}
labels:
k8s.kuboard.cn/name: certd-deployment
name: certd-deployment
namespace: certd
spec:
selector:
matchLabels:
k8s.kuboard.cn/name: certd-deployment
template:
metadata:
labels:
k8s.kuboard.cn/name: certd-deployment
spec:
containers:
- env:
- name: TZ
value: Asia/Shanghai
- name: certd_system_resetAdminPasswd
value: 'false'
image: 'registry.cn-shenzhen.aliyuncs.com/handsfree/certd:latest'
imagePullPolicy: IfNotPresent
name: certd
ports:
- containerPort: 7002
name: https
protocol: TCP
- containerPort: 7001
name: http
protocol: TCP
resources: {}
terminationMessagePath: /dev/termination-log
terminationMessagePolicy: File
volumeMounts:
- mountPath: /etc/localtime
name: localtime
readOnly: true
- mountPath: /etc/timezone
name: timezone
readOnly: true
- mountPath: /app/data
name: data
dnsPolicy: ClusterFirst
restartPolicy: Always
schedulerName: default-scheduler
securityContext: {}
volumes:
- hostPath:
path: /etc/localtime
type: File
name: localtime
- hostPath:
path: /etc/timezone
type: ''
name: timezone
- name: data
persistentVolumeClaim:
claimName: certd-data
---
apiVersion: v1
kind: Service
metadata:
annotations: {}
labels:
k8s.kuboard.cn/name: certd-deployment
name: certd-deployment
namespace: certd
spec:
ports:
- name: http
port: 7001
protocol: TCP
targetPort: 7001
- name: https
port: 7002
protocol: TCP
targetPort: 7002
selector:
k8s.kuboard.cn/name: certd-deployment
sessionAffinity: None
type: ClusterIP
status:
loadBalancer: {}
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
cert-manager.io/cluster-issuer: my-acme-issuer
labels:
k8s.kuboard.cn/name: certd-deployment
name: certd-deployment
namespace: certd
spec:
ingressClassName: nginx-ingress
rules:
- host: certd.k8s.lan
http:
paths:
- backend:
service:
name: certd-deployment
port:
number: 7001
path: /
pathType: Prefix
tls:
- hosts:
- certd.k8s.lan
secretName: certd-tls-secret
然后局域网访问certd.k8s.lan进入管理员
默认账号密码是admin 123456 记得修改
证书流水线的创建
首先的话创建一个流水线,我这里这么写:
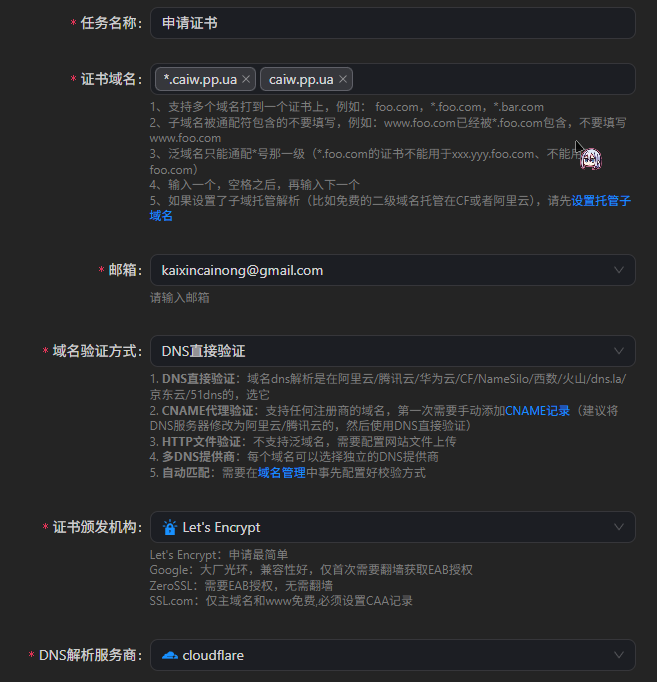
然后的话去CF申请一个Token,这里不过多赘述了
域名所有权验证有HTTP和DNS两种方式,DNS就是让ACME直接与权威DNS解析商通信确认有Challenge的解析
Http则无法申请泛域名,这里的话最适合我们的还是DNS Challenge
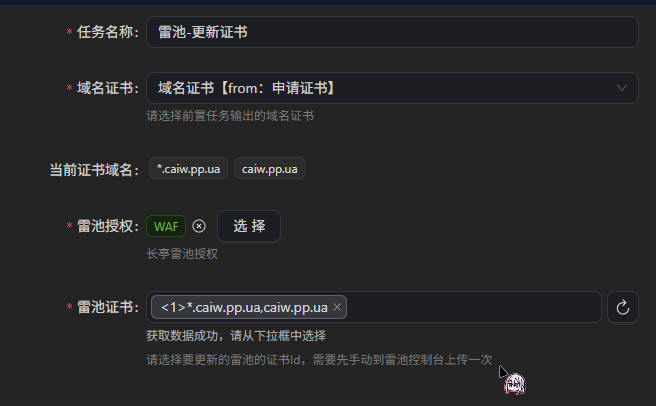
然后手动运行证书申请,把申请的证书先复制一份到雷池(伏笔)
然后选择部署到雷池 这么写就好
我真正想说的其实是通知的配置,也是比较有意思的
通知配置
我这边用的是bark,因为我用的iOS,Bark免费而且及其简单易用
我前面说过,Certd有些功能需要付费才能使用
真的是这样吗((
我们选择自定义web hook请求
Bark的API同时支持GET和POST
那不就简单了吗
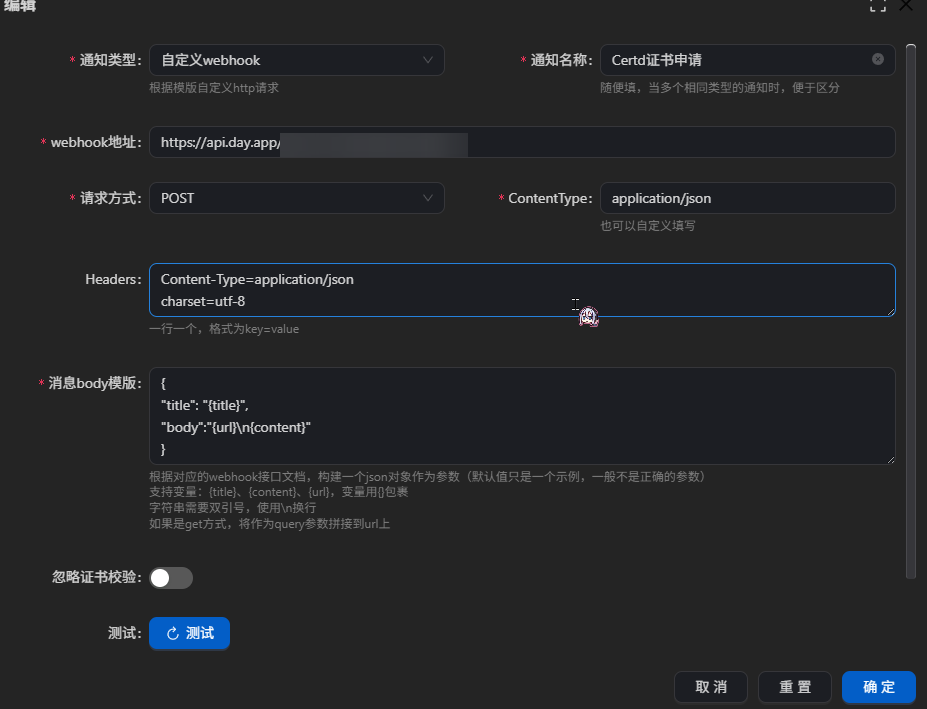
这么写就好了
那么能不能用呢
当然是可以的了()不然我也不会发出来